At the time of writing, the current offering of the Cross-Chain Interoperability Protocol (CCIP) by Chainlink is being combined with their new Confidential Compute Service. This should make it possible for institutions and developers to move tokens, invoke logic, or transfer data across ledgers without putting their respective details on the blockchain. (chain.link)

CCIP + Confidential Compute moves tokens and data securely, keeping details private (Image Source: Avark Agency)
Why That Matters Now
Before this application of Confidential Compute, the only areas that cross-chain products benefited had been the movement of value and data. These new products never locked down the secretly provided data or algorithms used within the transactions. This new technology shifts this practice because it provides the execution of the logic outside of the chain but within the tamper-proof environment of the enclave, with the logic and the data kept hidden, but the result being publicly recorded on the ledger. This result, combined with CCIP, can now move between the chains securely. This is the breakthrough.
Before the application of Confidential Compute, cross-chain products primarily benefited from the movement of value and data. These products never secured the privately provided data or the algorithms used within transactions. Confidential Compute shifts this practice by executing logic outside the chain but within a tamper-proof enclave environment. In this setup, both the logic and the data remain hidden, while the results are publicly recorded on the ledger. Combined with CCIP, these results can now move securely between chains. This represents a breakthrough in cross-chain operations.
A Quick Snapshot for Readers on the Move
- CCIP standardizes secure messaging and token routing across multiple blockchains.
- Off-chain operations are performed using Trusted Execution Environments (TEEs), keeping sensitive inputs confidential.
- Together, CCIP and Confidential Compute enable private cross-chain operations, including institutional token transactions and more.
What Business Problem Does It Help Overcome
Organizations value the transparency of blockchains but must also protect their business secrets. Banks, tokenized funds, payment management services, and supply chain companies cannot expose customer lists or pricing algorithms on public ledgers. At the same time, they seek the liquidity benefits of multi-blockchain ecosystems. CCIP combined with Confidential Compute closes the gap between transparency and privacy requirements, enabling both secure operations and protected data.
What Confidential Compute Is and How It Works
Confidential Compute can be visualized as a sealed box in which a trusted clerk examines privileged documents and generates a single publicly visible receipt. On the blockchain side, this sealed box corresponds to a hardware- or cloud-based Trusted Execution Environment (TEE), such as Intel Trust or AMD SEV. The environment safely executes the code outside of observers’ knowledge. As a result, a token transfer proof emerges and can be published on the blockchain. This analogy clarifies how sensitive logic and data remain confidential while producing verifiable outcomes.
CCIP + Confidential Compute + CRE: The Architecture
Chainlink provides CCIP infrastructure for cross-chain messaging along with institutional-level tools. Confidential Compute integrates with the Chainlink Runtime Environment (CRE) and oracle infrastructure, allowing developers to manage private off-chain calculations and relay verified results across chains. This delivers a familiar development experience while introducing a privacy layer precisely where it is needed.
CCIP with Confidential Compute lets developers run private logic and share results across chains. (Image Source: VeradiVerdict)
Practical Cases That Are No Longer Theoretical
Tokenized Funds with Restricted Access
A regulated fund might use Confidential Compute to facilitate fund redemptions that require private KYC and allocation logic. The allocation process runs off-chain, and CCIP transfers the resulting funds between ledgers. Only proof of compliance with the rules is published. Early institutional pilot programs and tokenization flows demonstrate this as a practical application.
Private DeFi Primitives Designed for Institutions
In institutional DeFi scenarios, lending pools can conceal sensitive details such as interest rate models or counterparty credit ratings while making final loans publicly transparent if required. Confidential Compute calculates sensitive metrics off-chain and publishes only the necessary state changes, enabling secure, private, and verifiable operations.
Cross-Border Payment Infrastructure That Honors Bank Secrecy
Banks can execute settlement logic within an enclave, perform value transfers across different chains using CCIP, and carry out reconciliation without revealing customer information. This reduces legal friction and facilitates regulatory compliance.
Security and Trust: What to Look Out For
Confidential Compute depends on Trusted Execution Environments (TEEs) and the concept of attestation. While TEEs are considered secure, they are not infallible. Firmware weaknesses can still occur, which is why hybrid architectures often combine hardware runtimes with cryptographic proofs, such as zero-knowledge proofs and multi-party custody mechanisms. Industry literature highlights these trade-offs and references solutions offered by Intel SGX and AMD SEV.
Developer Experience: What’s Different and What’s the Same
The construction of applications with Confidential Compute introduces less friction for developers. Chainlink’s goal for the Confidential Compute module of the Off-Chain AI platform is to make the service accessible via well-documented SDKs and the CRE orchestration layer.
This approach allows developers to deploy applications that integrate confidentiality oracles without overhauling their existing technology stack. Only the portion of the business logic that must remain confidential needs to be directed to the enclave. The rest of the application logic can remain on public blockchains while still enabling cross-chain transactions via CCIP.
Competition and Industry Context
Confidential computing has existed for several years, with cloud providers and CPU manufacturers offering Trusted Execution Environment (TEE) solutions. What sets 2025 apart is the maturity of TEE infrastructure combined with a messaging layer that treats privacy as a first-class concern. The scale provided by Chainlink as an oracle network, coupled with availability on 60+ chains via CCIP, gives it an edge over solutions that only offer enclave capabilities.
Regulatory Approach and Compliance
One reason institutions hesitate to move more operations onto blockchains is regulatory risk. Confidential Compute mitigates this concern by providing proof of results and auditable trails to regulators or auditors without exposing customer-level data. This combination of transparency and optional confidentiality aligns with the compliance requirements of financial institutions exploring blockchain adoption. Recent news on bank pilot projects and alliances demonstrates this growing interest.
With Chainlink Confidential Compute, you get:
• Private smart contracts as a new industry primitive
• A privacy-preserving data economy
• Compliance adherence with selective data disclosure
• Confidential interoperabilityThe result: Institutional onchain finance at scale.… pic.twitter.com/WHVD03szzO
— Chainlink (@chainlink) November 14, 2025
Early Collaborations and Pilot Indications
Public roadmaps from Chainlink and press releases from SmartCon show CCIP + Confidential Compute adoption pilots for tokenized asset flows and institutionally secure custody solutions. These pilots are significant because they move the technology from research concepts into real production patterns, revealing integration challenges early on.
User Experience: End User Benefits
Most users may not notice the difference directly, but they benefit in several key ways:
- Instant settlement of transactions
- Access to interchain liquidity
- Trusted institutional services previously operating at the fringes of crypto
Developers also benefit:
- Secure APIs
- Private calculations, allowing monetization of proprietary models without exposing them to competitors
This three-way benefit for users, developers, and institutions makes the CCIP + Confidential Compute combination highly catalytic.
Limits and Honest Caveats
No product can eliminate risk. TEEs must be continuously validated, and cross-chain messaging cannot introduce single points of failure. Standardizing attestation and auditing processes across cloud providers and hardware manufacturers will take time. Consequently, adoption of this technology will likely be incremental.
Developer Action Checklist
- Identify sensitive logic and data within your stack
- Map the chains involved in your workflow
- Implement prototype enclave-based computation for critical functions
- Use CCIP to relay verified messages and transfer tokens
- Design attestation and auditing schemes for regulators or customers
Deep Technical Integration: How CCIP and Confidential Compute Fit Together
CCIP manages messaging and value transfer across blockchains, ensuring that messages either reach the target chain or safely return. Confidential Compute provides a private execution layer for sensitive inputs and business logic within an attested enclave environment. Only results serving as proofs exit the enclave.
To illustrate, imagine CCIP as a rail system and Confidential Compute as a secure vault attached to the carriage. The vault processes private instructions, generates a sealed receipt signed by the enclave, and hands the receipt to CCIP. CCIP then transfers the receipt across the blockchain rail system. The smart contract on the receiving chain treats this receipt as the authoritative result.
The Chainlink Runtime Environment (CRE) orchestrates oracles, CCIP routing, attestation verification, and development workflows under a single control plane. CRE serves as an application runtime environment, allowing teams to create workflows containing compute tasks and CCIP messaging without complex integration overhead.
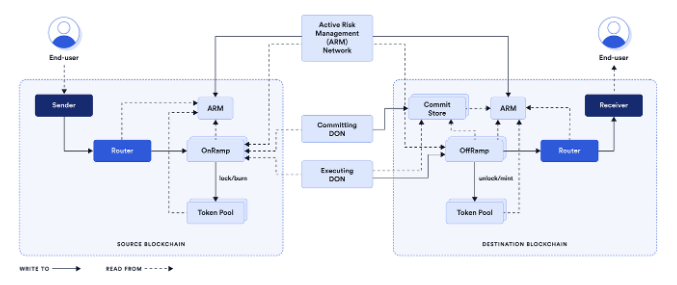
CCIP moves messages, Confidential Compute keeps data private, and CRE coordinates it. (Image Source: Medium)
Security Model: Trust, Attestations, and Multi-Party Resilience
Confidential Compute relies on two types of assurances:
- Hardware Attestation:
This involves creating a cryptographic proof that the expected code executed on real TEE hardware within the enclave. Validators and smart contracts verify this proof before accepting execution results, ensuring the compute source is reliable. - Protocol-Level Redundancy:
To reduce single-source dependence, the system promotes multi-enclave or multi-provider execution. Independent attestors, threshold signing, and cryptographic proofs (like zk-SNARKs or aggregated signatures) enhance security. Chainlink’s architecture supports hybrid attestation, high-performance TEEs combined with cryptographic primitives.
Caveats:
TEEs remain vulnerable to real-world attacks such as side-channel, supply chain, and firmware exploits. Institutional users, therefore, require multi-vendor attestation and transparent incident handling. Scaling TEEs with Confidential Compute, cryptographic proofs, and multi-party computation is detailed in the whitepaper and CRE documentation.
Implementation Patterns: Practical Templates
These patterns are immediately implementable by development teams and integrate with CCIP routing:
- Private Token Transfer (Institutional Redemption Flow):
- The enclave executes allocation logic and generates a transfer proof to meet AML obligations.
- CRE forwards the proof via CCIP to the custody smart contract on the target blockchain.
- The contract receipt confirms attestation before fund transfer.
- Custody and KYC remain off-chain; the settlement layer is auditable and cross-chain.
- Secret Oracle Aggregation (Private Market Data):
- Enclave aggregates multiple encrypted data streams to calculate an index without exposing individual feeds.
- Only the final index and attestation are published.
- CCIP disseminates the attestation to consumer chains, allowing commercial distribution while preserving data owner privacy.
- Confidential On-Chain Settlement of Regulated Transactions:
- Trade matches and margin calculations occur inside the enclave.
- Results generate settlement instructions and compliance receipts.
- CRE uses CCIP to publish receipts across exchange and custody ledgers.
- This ensures regulatory audibility while maintaining counterparty confidentiality.
Performance and Cost Realities
- TEEs offer near-native performance, which is critical for low-latency institutional trading.
- Enclave and CRE setup incurs additional costs for hardware and attestation oracles.
- Deployments will balance speed, cost, and threat models. TEEs handle high-speed needs, while cryptographic proofs cover high-risk flows.
- Chainlink emphasizes a staged approach: address business needs with TEEs first, then improve cryptographic assurances later.
Real-World Signals: Who’s Testing and Why It Matters
- Lido: Uses CCIP for cross-chain wstETH transactions, demonstrating scalability.
- SBI Digital Markets and partners: Experiment with CRE and private workflows for custody and tokenization, signaling institutional interest in privacy.
- SmartCon / Press Releases: Show tokenization pilots with major financial institutions, highlighting demand for auditable, private cross-chain transactions.
These pilots indicate that financial institutions will bring compliance requirements, operating discipline, and genuine settlement activity, encouraging broader adoption by other participants.
Governance and Compliance: The Role of the Regulator
Confidential Compute balances client data confidentiality with regulatory auditability. Regulators can oversee operations without accessing sensitive client data.
- Regulators receive time-limited access tokens or receipts.
- Enclaves record cryptographic proofs of audits and generate deterministic audit trails.
- Compliance workflow hooks are offered by CRE and Chainlink’s Proof of Reserve/ACE.
- The outcome: more regulators can enable on-chain settlement without requiring full access to client data.
Confidential Compute lets regulators verify activity without exposing client data. (Image Source: Datamam)
Also Read: How Baidu’s ERNIE 5.0 Sets a New Standard: Exploring the Rise of Omni-Modal AI Models
Developer Quick-Start
This is a conceptual workflow, not a copy-and-paste SDK:
- Construct individual logic as an enclave-capable module.
- Deploy the module to CRE with attestation metadata.
- Call CRE with private inputs encrypted.
- CRE returns an attested result signed by the enclave.
- Send the attested result via CCIP to the target chain(s).
- Receiving contracts confirms the attestation and consumes the result.
Specific APIs and CRE SDK examples must be followed to avoid low-level TEE errors.
Practical Rollout Roadmap: Cautious Optimism
Phase 1 – Closed Pilots: Permissioned environments with white-glove integration and limited CCIP routes.
Phase 2 – Permissioned Production: Cleared institutions execute production workloads with integrated custodians and auditors. CRE becomes a utility for tokenized assets.
Phase 3 – Mainstream Usage: Advanced privacy primitives (Hybrid TEE + ZK stack) and multi-provider attestation emerge. Retail DeFi applications begin building interoperable, privacy-preserving functionality.
This ensures secure adoption without assuming upfront trust in developers.
Conclusion
The combination of CCIP, CRE, and Confidential Compute enables private, interoperable applications. It lowers institutional onboarding costs, allows developers to monetize proprietary logic, and provides users with faster, privacy-preserving settlement.
By merging the cross-chain rail (CCIP), orchestration/runtime environment (CRE), and a confidentiality layer (Confidential Compute), pilots scaling with multi-party attestation could mark 2025 as the turning point when cross-chain infrastructure evolves from experimental plumbing to institutional-grade platforms.
Frequently Asked Questions
- When will Confidential Compute be available?
Later this summer, with early access and pilot programs already underway. - Do TEEs require trusting cloud providers?
You trust the hardware/firmware, mitigated by multi-enclave setups and independent attestation. CRE supports multi-party and multi-provider scenarios. - Is a hybrid stack possible?
Yes. Sensitive logic stays in the enclave; only verified results are published publicly. - How do auditors confirm private runs?
Auditors receive signed, time-limited attestation records and, if needed, decrypted excerpts under NDA. - Immediate risks?
Supply chain or firmware exploits, faulty attestation checks, and single attestor dependence. Mitigated via multi-provider attestation, audits, and gradual rollouts. - What is CCIP?
Cross-Chain Interoperability Protocol is a messaging and value transfer standard across blockchains. - Confidential Compute vs End-to-End Encryption:
Encryption protects data in transit/at rest; Confidential Compute secures data during code execution, inaccessible even to the host. - Will institutions trust TEEs?
Yes. Trust grows with attestation, audits, and multi-vendor strategies. - Can public DeFi interact without seeing private inputs?
Yes. Confidential Compute produces verifiable outputs; CCIP broadcasts them to chains without revealing original inputs.

