The Fundamentals: What All Readers Need To Know Now
Quantum computers are developing quickly enough to change blockchains’ security math today. Super-powerful error-corrected computers will eventually be capable of decrypting the asymmetric cryptography that protects signatures and wallets, the same encryption that Bitcoin, Ethereum, and millions of wallets rely on. The industry can no longer consider this a theoretical threat: vendors and standards bodies are moving now to make systems stronger with post-quantum algorithms and quantum-immune ledgers. (csrc.nist.gov)
NIST, America’s standards body, has already begun public policy and planning for rollout by selecting and standardizing post-quantum algorithms, the moment when companies should begin making plans to migrate. While that is happening, quantum hardware teams provide incremental error correction advances and larger chips, keeping pace with the attack horizon in the wild. All these developments force crypto engineers to react now: move keys, design upgradable signature schemes, and protect stored crypto material from “harvest-now, decrypt-later” attacks. (NIST PQC project)

Quantum is racing toward breaking today’s crypto. The industry must upgrade now. (Image Source: Forbes)
Why Blockchains Appear To Be Under Threat And Why Keys Are Not Interchangeable
All public blockchains rely on elliptic-curve signatures (ECDSA or equivalents). Those cannot be efficiently compromised by privacy-classical computers. A quantum computer running Shor’s algorithm can factor, or break discrete logs, and thus allow an attacker to “siphon off” private keys from a public key and spend funds. The threat is double-edged:
- Active stealing: an offensive quantum machine can steal private and zero-balance keys.
- Harvest-today, decrypt-tomorrow: those who are against it can harvest today encrypted data or authenticated transactions and decrypt it when they possess a powerful quantum machine. Institutions fear that data harvested today can be read tomorrow. (csrc.nist.gov)
But all crypto objects weren’t created equally open. Addresses that never had a public key exposed, i.e., one-use addresses where public keys are only disclosed on spend, are more secure for longer. Custodians, exchanges and long-term storage that possess public keys or have signed messages are the first to get pinched. Those assets are value targets. (OneSafe)
Where The Response Is Happening: Standards, Software And Quantum-Native Chains
Three things are happening at the same time that characterize the defensive landscape today:
- Algorithms and standards. NIST’s post-quantum cryptography (PQC) project has identified and started standardizing quantum-resistant algorithms, offering deployable migration recommendations to libraries and protocols. That work offers implementers an operational roadmap and not a set of academic options. (NIST PQC project)
- Client and protocol upgrades. Wallet and node software must be able to support new signature schemes. Hybrid schemes, PQC + classical, for forward quantum security compatibility. Hybrid signatures have already been tried in testnets by vendors and projects. The engineering problem is to make secure, transparent and auditable upgrades to billions of value locked up.
- Post-quantum-resistant chains and projects. There are post-quantum-resistant chains in nature, using hash-based or other signature schemes. There are some of these old Layer-1s and older projects that add post-quantum primitives to the stack. They are trying to win over users who care about a quantum attack someday down the road. (qanplatform.com)
The Short Technical Playbook Crypto Teams Are Working With
Fundraising infrastructure teams and infrastructure teams as a whole usually have the following three things in mind:
- Inventory and risk triage. Note where long-lived secrets are stored in keys, cold storage and backups. Custodians and exchanges are of the highest priority because they hold aggregated keys.
- Patchable cryptography. Trending toward wallet and protocol designs that support new signature schemes without chain splits. Hybrid signatures (classical + PQC) act as a bridge solution.
- Store archives. Quantum-resistant envelopes encrypt stored keys and signed documents where appropriate; anticipate that attackers will have copies to decrypt in the future. (csrc.nist.gov)
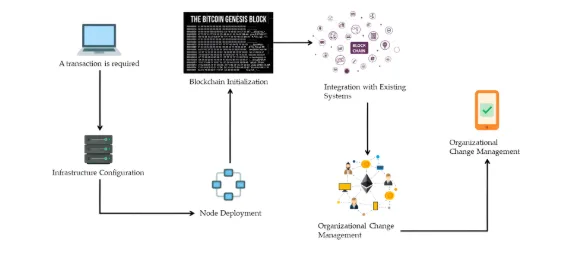
Mapping risks, upgrading wallets, and securing stored keys for the quantum era. (Image Source: MDPI)
The pragmatic school of thought regards migration as an engineering problem, a problem that will necessarily include cryptographers, wallet implementors, custodians and governors.
A Short Vignette: Why A Treasurer’s Sleep Is Lost
Let’s assume a corporate treasury stores cold backups of private keys and signed settlement instructions for a couple of years. Their security experts find out that nation-state actors may maybe quietly preserving blockchain snapshots and internet traffic. Within a decade, if they have a good quantum-capable competitor, they have the cachet. The treasurer knows that if they simply sit on their hands, today’s backups are liabilities tomorrow. The answer is operational: switch keys, apply post-quantum wrappers to backups and commit vendors providing hybrid signatures. That tension makes abstract mathematics a boardroom gauge of risk. (Industry trends-based reporting and advisory piece.) (The Times)
Where There Is Doubt: Schedules And Feasibility Of Attack
Quantum machine breakdown. Estimates for blockchain crypto depend on hardware progress and error correction. Top labs continue to drive incremental advances in Google error correction and current work on chips shows gigantic advances, but scalable, usable quantum attacks require more engineering. Experts have wonderfully wide sets of timelines; that keeps defense planners concerned about the threat as an engineering and policy problem rather than an unadulterated research problem. (blog.google)
Most importantly, uncertainty creates risk. Danger can play the harvest-now game because it will be able to decrypt later. That behavior raises the felt sense of urgency for organizations that store sensitive data in warehouses or manage large sets of private keys.
INCORRECT. WRONG. FALSE.
It’s normal for one to believe BTC can be “cracked” by quantum computing. I understand. The media also brainwashed people into taking an experimental vaccine and had people wearing masks inside their cars but I digress.
Here are the facts.
There are… https://t.co/x37Lgtbd4x pic.twitter.com/0Q21qRp3Rg
— 941 (@level941) October 17, 2025
Early Winners And Losers Who Benefits From Doing It Now
Winners: exchanges, custodians, enterprise wallets and middleware that leap early on PQC. They will be able to sell higher-value guarantees and avoid expensive emergency migrations in the future.
Losers: services and protocols that bake signatures into non-upgradeable contracts. If a chain can’t realistically alter signatures without an unpopular hard fork, it’s weaker in the long run.
While a tooling vendor ecosystem hybrid-signature wallets, key-rotation services, PQC libraries will be in hot demand as migration becomes mainstream. (PostQuantum.com)
wallets break at the multi-chain boundary because private keys are protocol-local. @wardenprotocol moves keys into programmable policy accounts that can own btc/eth/cosmos signers under one engine. agents set rate limits, time locks, role-based approvals, social recovery,… pic.twitter.com/0qdZTNSZLl
— DucKhoaⓂ️Ⓜ️T (@DucKhoa96) October 16, 2025
Technical Deep Dive What Engineers Actually Need To Change
The technical foundation issue is straightforward to articulate: substitute or augment quantum-breaking-vulnerable public-key computations (basically Shor’s algorithm). In reality, that transition touches a great many pieces of moving machinery across wallets, node code, smart contracts and archive habits.
- Signature schemes first. Most blockchains use elliptic-curve signatures (ECDSA, Schnorr forms) whose security rests upon the discrete-log problem. Post-quantum alternatives are families: lattice-based, code-based, hash-based and multivariate schemes. All there is a trade-off: key sizes, signature sizes, verification performance, implementations maturity. NTRU-like, Kyber-like lattice schemes typically have optimal performance and sacrifice good key/signature sizes at present moment. Hash-based ones (XMSS, LMS) are seemingly simple and traditional but require more stringent operation requirements (e.g., stateful keys). Engineers must trade off against throughput, storage and UX constraints.
- Protocol upgradeability. Upgrade procedures already inherent within the protocol indicate a blockchain’s ability to modify signature schemes without forking. There are feature flags or soft forks in some chains that can enable new verification rules in a backwards-compatible manner. There are others that require hard forks an operationally and politically precarious route. In practice, communities would like hybrid signatures at transition point: a transaction or an account would need to meet both classical and post-quantum signature. That approach eschews sudden discontinuity while building instant, layered security.
- Wallet lifecycle and key keypoints. Wallets must support key rotation, multi-algorithm keysets and hybrid signatures. Most importantly, hardware wallets and HSMs must be hardened to PQC primitives; that will require firmware updates, supply-chain attestation and new test paradigms. Cold backup formats must be re-written: storing keys without quantum-resistant crypto for long-term purposes introduces harvest-now risk. Hide stored secrets in quantum-safe wrappers (post-quantum KEMs or multi-layered encryptions) to limit that exposure.
- Immutability and smart contracts. Smart contracts that involve verification logic on-chain escrow signature validation or multisig validation must have the ability to foresee upgrade paths. Smart contract code that is immutable implies that teams must author future-proof contracts that invoke external verification libraries (upgradable libraries) or verification oracles that are upgradable primitives. Where immutability is a barrier to updates, the protocol must have migration tools to port state into upgradable scaffolds.
- Surveillance and archives. Organisations need to anticipate adversaries to store backups of data on-chain today to decrypt in the future. That dark reality changes archival practice: encrypt stored sensitive information with quantum-resistant methods and limit the lifetime of keys used to protect long-lived assets.
Migration Patterns Phased, Risk-Based, And Hybrid
A realistic migration has three phases: assessment, hardening, and migration.
Assessment (0–6 months for an active programme)
- List all cryptos held: hot keys, cold keys, backups, multisig members, contract-imbedded keys and third-party vaults.
- Prioritize risk: custodians and exchanges first, long-term archives second, then retail wallets.
- Test PQC libraries and measure performance on target hardware (HSM, mobile, node).
Hardening (6–18 months)
- Enforce hybrid signing on high-risk routes. Hybrids mix a traditional scheme with a PQC scheme; a transaction determines which one or both dominate via policy. Hybrids allow real-time security with incrementally depreciating legacy-only verification.
- Update wallet code and hardware wallet firmware to support PQC key generation and signing.
- Reformat backup forms to support quantum-resistant envelopes and rotate keys on an accelerated schedule.
Migration (18–36 months and ongoing)
- Move custodial pools and contract states into PQC-ready schemes through extensively tested migration bridges.
- Eliminate classical-only verification from new-minted addresses but retain read-only legacy support on inherited addresses as necessary.
- Publish proofs of custody and attestation reports illustrating PQC uptake to customers and regulators.
This risk-based pace recognizes resource limitations. A billion-dollar exchange cannot afford to wait for optimal standards; it must go now with hybrid schemes and rollouts under control.
Protocol Case Studies Realistic Portrayals, Not Prescriptions
Bitcoin-style chains: These chains are derived from public keys and, in typical deployments, expose just public keys on spend. This design exposes there with short latency to exposure: spent public keys of UTXOs are more vulnerable. For custodians of client UTXOs, rotation and migration to multisig are paramount. A pragmatic solution is to incorporate hybrid multisig schemes and migrate assets into new address types that authenticate with PQC-enabled stacking.
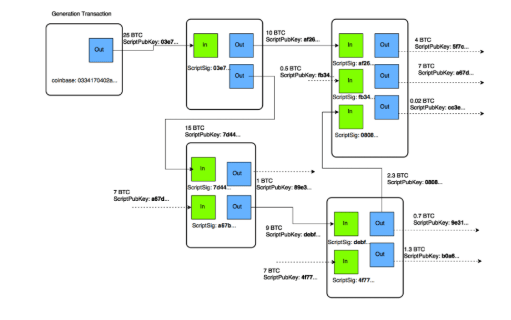
Spent keys expose Bitcoin UTXOs, driving a shift to PQC multisig. (Image Source: MDPI)
Smart-contract platforms (Ethereum-type): Smart-contract platforms prefer keeping verification logic inside contracts. Institutions in this category possess both technical and governance dilemma: alter the protocol or alter contracts. The majority of the developers use upgradable contract structures invoking a verifier contract; replacing the verifier with a PQC-variant freezes a large portion of contracts without altering them all. The primary effort in operation comes from testing and synchronization between DeFi governance institutions.
Quantum-native chains: Certain protocols are quantum-resistant from the foundation with hash-based or other PQC primitives. They raise an interesting interoperability and custody question they can offer instant quantum-resistant rails but need to work out liquidity, developer tooling and long-term security auditing in order to be trusted.
Sidechains and Layer-2s: Most Layer-2s must inherit base-layer cryptography, so there must be a consensus on stack upgrades by communities. Hybrid schemes may be employed by certain rollups in their sequencer and withdrawal proofs before base layers can modify core consensus rules; that staging can provide strategic user protections.
Implementation Checklist Hands-On Steps Ops Teams Can Take
- Inventory: private keys, KMS, HSM, backups and contracts with embedded verification.
- Risk score: risk per value-at-stake, exposure duration, public-key exposure.
- Test PQC: test candidate PQC libraries (latency, signature size, key size) on your hardware.
- Hybrid deploy: deploy hybrid signatures for performance-sensitivity paths and mark them behind feature flags.
- Key rotation plan: frequency and automation for multisig members and custodial pools.
- Backup re-encryption: rewrap archival backups with quantum-resistant key-encryption schemes.
- Firmware supply-chain: confirm firmware upgrades for hardware wallets; require vendor attestation.
- Smart contract gateway: move contract verification to an upgradeable verifier where possible.
- Audit & insurance: coordinate PQC audits and expand quantum-risk cover disclosure insurance.
- Stakeholder comms: publish migration timetables for regulators and customers; transparency avoids panic and trust is established.
Migration doesn’t only challenge engineering, it challenges governance. Custodians have a fiduciary duty: they must explain migrations to clients and regulators. Regulators will require risk assessment and ensure migrations do not put client funds at risk. Boards must authorize PQC adoption budgets and provide evidence of competent third-party audits.
Legal encumbrances on token ownership may require custodians to ensure chain integrity. Any migration that changes token semantics needs to be legally examined rigorously and technically attested.
Also Read: Are Crypto Privacy Coins Still Relevant in 2025?
Frequently Asked Questions
- Q: What is the importance of migration for average users?
A: Low in importance for ordinary traders who send addresses and do not reuse keys. High importance for custodians, exchanges and anyone with long-lived backups or entitlement schemes. - Q: How costly will migration be?
A: It depends. Migration for large custodians will be tens of millions (engineer, audit, hardware upgrade, insurance). Small projects are less in absolute cost but have budget for library license, test and key-management changes. - Q: Simple using NIST standards?
A: NIST does simplify algorithm selection, so there is less ambiguity. Operability complexity and firmware/hardware uptake still remain, though. Standards make algorithm selection easier; implementation and deployment still require engineering effort to implement. - Q: Are there PQC-compatible hardware wallets?
A: Some vendors intend to release PQC firmware updates, but the timing differs. Customers should be comforted by vendor advice and prefer wallets that share their secure firmware update procedures and attestation openly. - Q: Can we rely on hybrid schemes indefinitely?
A: Hybrids are temporary defense. Ultimately, responsibility is handed over to grown-up PQC primitives and minimal classical trust. But hybrids do buy safe breathing room as ecosystems cohere. - Q: Must retail crypto holders panic?
A: No. To the average retail user today risk is low, especially if you don’t reuse addresses and keep private keys safe. More short-term risk is on custodians and cold storage backups. (OneSafe) - Q: Are blockchains upgradable to post-quantum signatures?
A: Yes several are, but upgrades have to be highly coordinated. Hybrid designs decrease risk of migration. NIST standards simplify migration decisions. (NIST PQC project) - Q: Is quantum attack a near term threat to Bitcoin or Ethereum?
A: Not near term as ongoing public attack, but both networks need to plan for migration. “Harvest-now, decrypt-later” makes it advisable to plan today. (blog.google)
Last Comment Employ Quantum Risk As An Engineering Timeline, Not An Emergency Option
Quantum crypto isn’t a daily prank on the front pages today but is relevant to longer-term risk planning. The smart strategy integrates quantum preparedness into routine crypto protocols: inventory, patch, rotate, audit, document. Early movers establish technical resilience and market confidence. Late movers threaten rushed, weak migrations under coercion.
If that’s your preference, I can reformat the implementation checklist into a project plan with timelines, milestones and suggested tooling (HSM vendors, PQC libraries, testnet designs). Do you want a one-page executive action plan or technical sprint plan for the engineering team?